Buffer Overflow in upload.cgi of iptime_nas_1.5.04
Buffer Overflow in upload.cgi of iptime_nas_1.5.04
The principle of the vulnerability
It can be observed that the vulnerability is caused by strcpy. Since the authentication logic is executed after the strcpy operation, this constitutes a pre-authentication vulnerability.
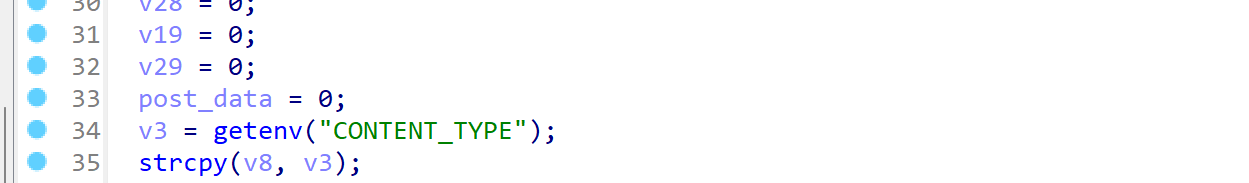
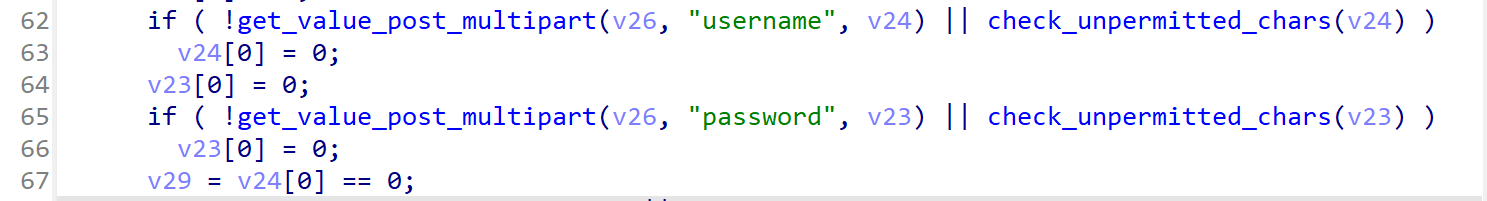
Use QEMU for simulation
1 | |
poc:
1 | |
The result of the attack.
It can be seen that the stack space allocated by V8 is 08h.
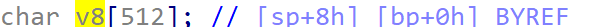
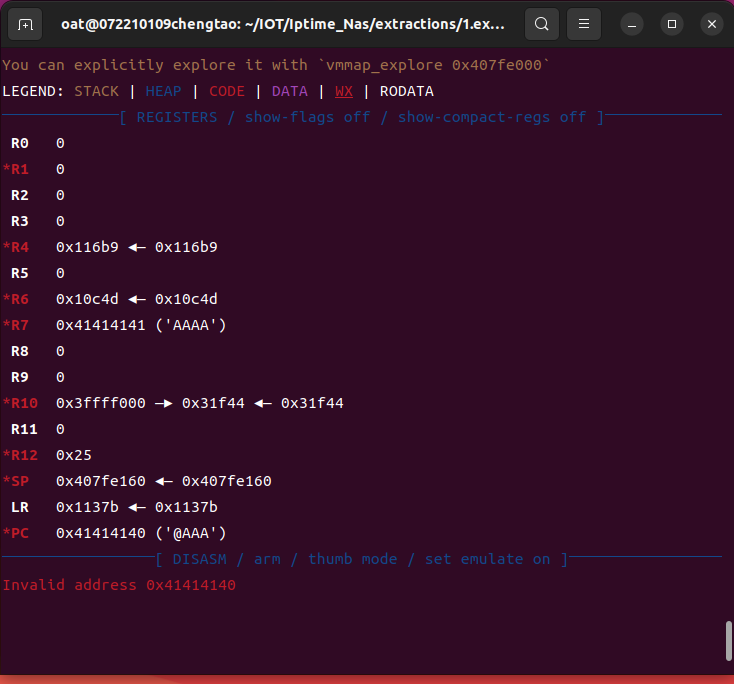
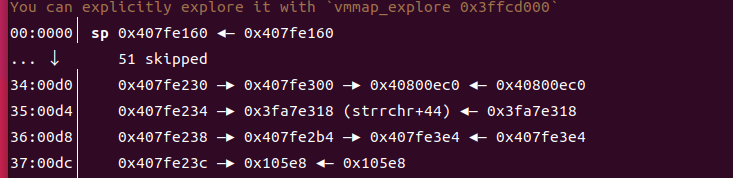
Eventually, the overflow reaches 0xd0, and the execution flow of the program is controlled. If necessary, more overflow can be achieved.
Buffer Overflow in upload.cgi of iptime_nas_1.5.04
https://lafdrew.github.io/2025/04/25/Buffer-Overflow-in-upload-cgi-of-iptime-nas-1-5-04/