web_acl_bindEdit_post-bindEditMACName-StackOverflow
web_acl_bindEdit_post-bindEditMACName
During my internship at Qi An Xin Tiangong Lab, I discovered a stack overflow vulnerability in the Planet router.
By analyzing the dispatcher file in the bin directory, I found that the function web_acl_bindEdit_post contains a stack overflow vulnerability.
The stack overflow can be triggered by bindEditMACName key value, which leads to a strcpy stack overflow.

In the main function, there is an account authentication detection. We create a cookie_0 in the tmp directory, with the content of “20 0 0”, and its function is to create a cookie with sufficient permissions to access this route.
1 | |
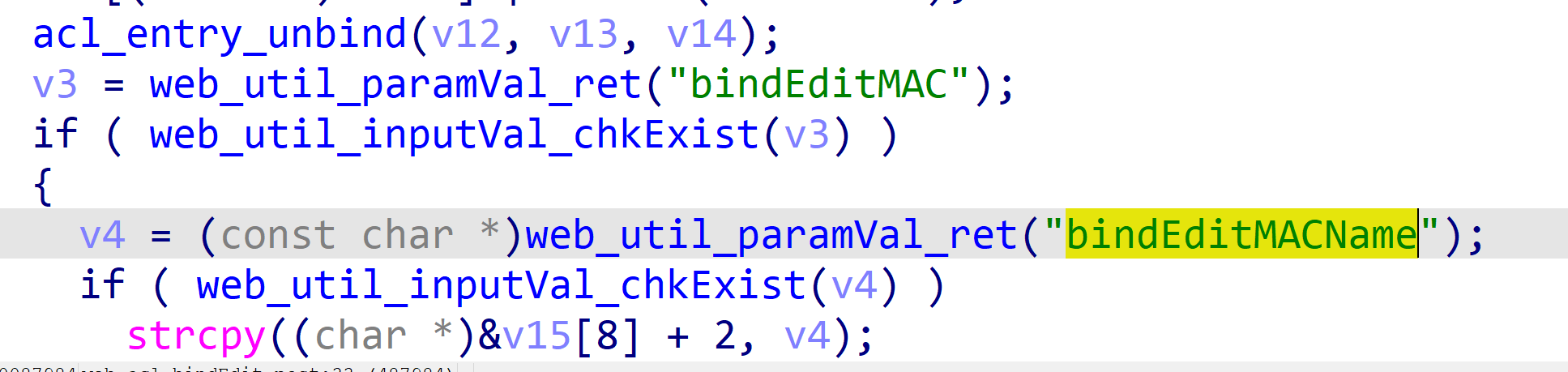
可以看到代码中存在由strcpy造成的栈溢出
How can we simulate a router
The content of the poc.py file is as follows:
1 | |
Attack result


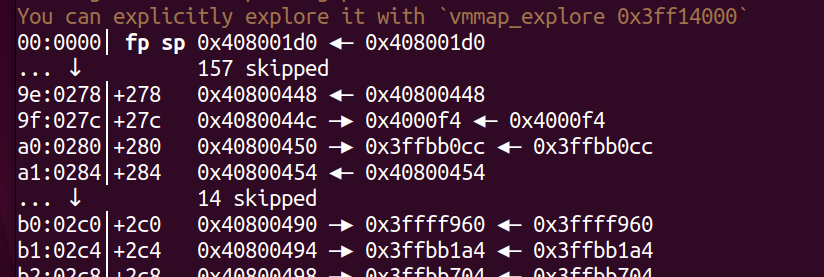
Through the above image, we can see that we have overflowed to 0x278 and successfully hijacked the control flow. If necessary, more can be overflowed.