Remote Command Execution in adm.cgi of wavlink-WL-WN579A3 Device
Wavlink-WL-WN579A3 introduced
Wavlink-WL-WN579A3 is engineered to deliver dual-band signal extension and expansive coverage, making it an exceptional solution for homes, offices, and hybrid indoor-outdoor networking environments. Equipped with a built-in high-power amplifier, this high-performance Wi-Fi range extender effortlessly penetrates thick walls and obstacles, ensuring stable connectivity across large areas.

Description:
A command injection vulnerability exists in the network configuration management module’s CGI script (./etc/lighttpd/www/cgi-bin/adm.cgi). The flaw is triggered when user-supplied input is concatenated and passed to the system() function via the sub_4018E8 routine. This module manages various WAN interface configurations (e.g., DHCP, PPPoE, 4G, PPTP/L2TP).
exploit:
The vulnerability occurs at code address 0x0040300C
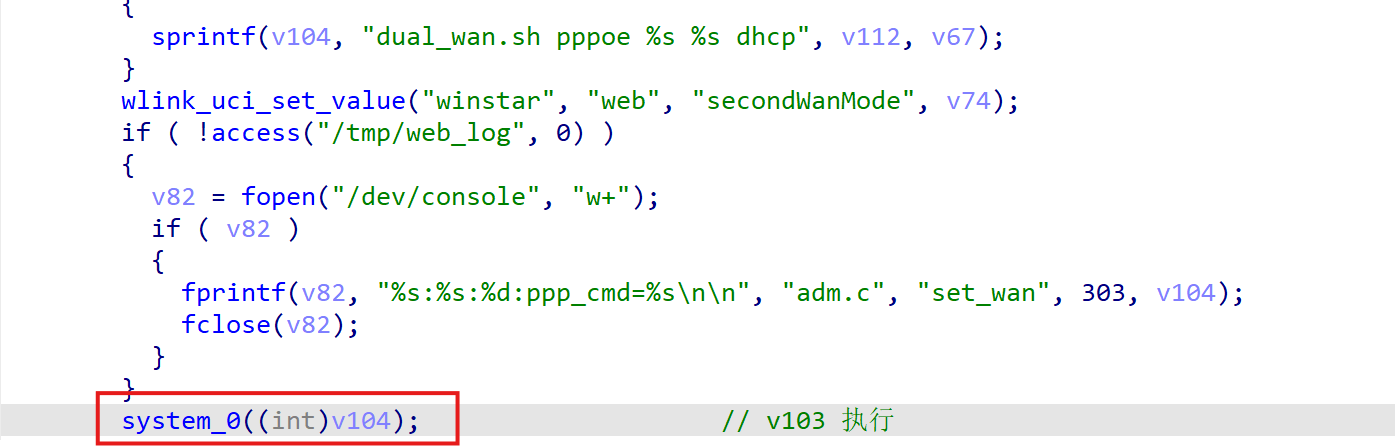
with the critical string construction performed at 0x00402EA8, where several parameters (such as v112, v67, v79, v111, and v81) are fully user-controlled.


Under specific conditions—when the HTTP parameters include:
1 | |
—and the POST data is crafted as follows:
1 | |
Executing within a chrooted QEMU environment:
1 | |
Debugging confirms execution within system()
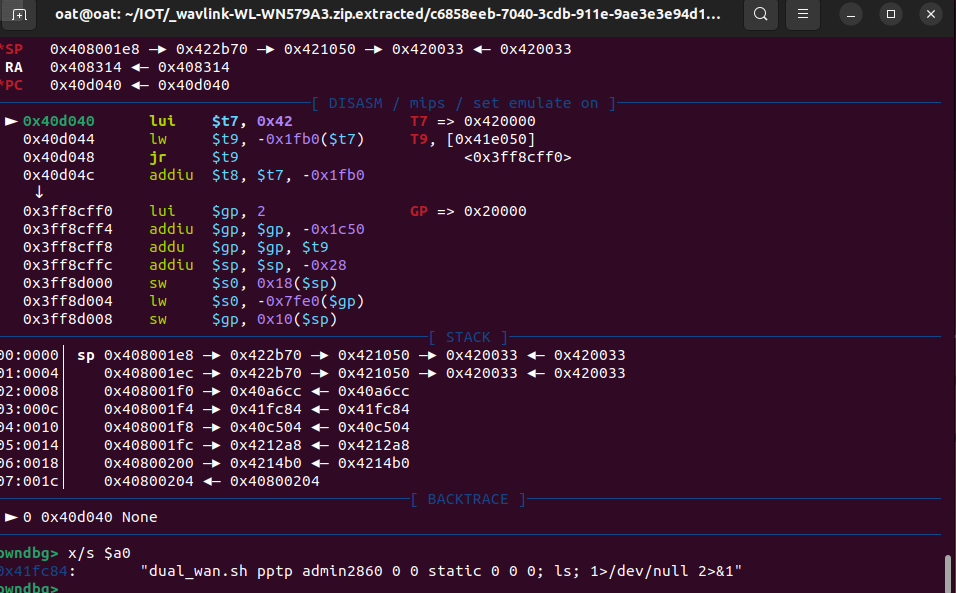
—the resulting command assembled by the application is:
1 | |
This command not only executes the intended script (dual_wan.sh) but also the injected ls command, which confirms that arbitrary command execution is possible. Given the potential for information disclosure and further system compromise, this issue is critical and should be addressed promptly.